Understanding Linux file permissions.
If you are a Windows user, Linux file permissions and commands like chmod may appear complicated and bizarre to you. That's not really logical, because file permissions exist on Windows, too. The major difference probably is that as Windows user you normally haven't to deal with them (except, that you have to give administrator confirmation when you want to store a file in some Windows directory). The reason for this is that Windows has been created as a single-user system, whereas Linux has to be considered as a multi-user system, even if you are the only one using the Linux computer.
Lets start with having a look at this famous root, not the top of the Linux file system (/), but the user with this name. Lots more than an administrator on Windows, the Linux "super-user" root has unlimited power; they may access any file and do with it what they want. That gives them full control of the system, but obviously working as root is also a big danger, because you easily could delete important system files. Thus, you should never log in to your Linux system as root, especially not on a machine with graphical desktop!
As a difference with root, the rights of all other users are limited. Their rights to access a given file or folder are governed by the actual file permissions of this given object.
Linux users are members of one or more user groups. When you install a Linux operating system, the user that you create during setup will be affected to a group with the same name as the user. This group will get the rights defined by default for the Linux distribution that you are using. On some distributions, the user is automatically added to some of the predefined Linux groups, on others you are asked for the groups that you want to add your user to. On Ubuntu, for example, the user that you create is automatically added to the group sudo (this group is called wheel on other distributions). Users who are members of this group have the right to execute the "sudo" command, i.e. to run a command or program with the rights of the super-user. This allows them to execute commands that normally they haven't the right to run (for example, install new software) and modify files that normally they may only access in read-only mode (for example, configuration files in /etc).
An important concept to understand when talking about file permissions is the ownership of a file. Globally, we can say that all files created in the home directory of user "allu" have user "allu" as owner (user), and group "allu" as owner group. Files in /bin, /etc, ... have root as owner. Note, that if you copy a file from one of these directories to your home directory, you become the owner of the file copy.
Owner user and owner group of a file may be changed using the commands chown (change ownership) resp. chgrp (change group). This is something that is rarely done, and it will not be discussed here...
What we will discuss here are the file permissions. These are stored with the files, thus they may be individually set for each directory and each file. The file permissions control which actions can be performed by which users. The three possible actions for every file are: Read (r), Write (w), and Execute (x).
Notes:
- On a Windows system, a file is supposed to be executable, if the file name has an adequate file extension; this extension is normally .exe, but there are other extensions used with executables, for example: .msi (Microsoft installers), .bat (batch files). On Linux, there isn't any extension for executable files. Being executable is a file permission just as being readable or being writable.
- In the case of a directory, Execute means being accessible, i.e. you can enter ("cd" into) the directory.
The 3 file actions (read, write, execute) may be individually set for 3 categories of users: a User (u) (the file owner), a Group (g) (the group, the file owner is member of), and Other (o) (users who are not part of the owner group). This means, that for each file and each directory there are 3×3 flags (that may equal True, for permission granted, or False, for permission denied) that rule the permissions on this object.
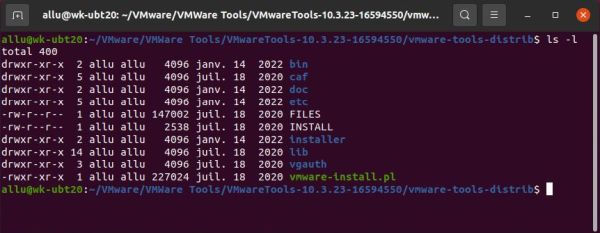
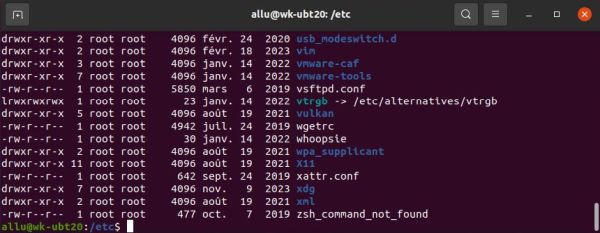
Lets have a look at the directory listings on the screenshots below. It has been created using the ls -l command, where the -l option means "long format", displaying detailed information about the file. On the left, we have the listing of a directory, being located somewhere within user allu's home directory. On the right, we have a part of the content of the directory /etc.
|
|
In the permissions listing the first character is either "d" (directory), "l" (link), or "-" (file). Then we have the 3×3 permission flags: r, w, x for User; r, w,x for Group; r, w, x for Other. If the action letter is shown, the permission is granted; if there is a "-" instead, it is denied. The owner of the files on the left screenshot is user "allu" and the owner group is group "allu". The file permissions listed for User and Group are thus those for user "allu" and group "allu". The files on the right screenshot, on the other hand, belong to root. Thus the permissions for user "allu" are those listed for Other.
The permissions listed here are typical for Linux systems. The permissions for directories normally are
rwx r-x r-x
what means that the owner has read and write access, whereas the group and all other users may only enter the directory and read its content.
The permissions for files (normal files resp. executables) normally are
rw- r-- r--
rwx r-x r-x
what means that standard users may modify the files in folders that are part of their home directory, but only root can modify the files in directories as /bin, /etc...
You will notice this, for example, when you want to modify a configuration file located in /etc using a text editor. As you haven't write access to /etc, you'll have to save the modified file to your home directory. Then, in a terminal, acting as super-user, you can copy the file back to /etc (sudo cp ...).
To change the permissions of a file or directory , we use the command chmod. In symbolic mode, the file permissions to be set/reset are indicated by three groups of actions (for the 3 user categories and indicated by the corresponding letter), separated by commas. The actions are one or more of Read, Write, Execute (indicated by the corresponding letter) and prefixed by a "+" to grant the permission, or a "-" to deny it.
Lets take an example. Suppose that we want to grant read, write, and execute permissions to User, and read-only permission to
Group and Other for the file setup.sh. Here
is the command:
chmod u+r+w+x,g+r-w-x,o+r-w-x setup.sh
To only change the three User permissions and the Group and Other read permission
(letting the other permissions as they actually are), the command is:
chmod u+r+w+x,g+r,o+r setup.sh
Other example (continuing with the file from above): Granting Group the execute permission and revoking the read permission to
Other:
chmod g+x,o-r setup.sh
Note that chmod is rather flexible, concerning the syntax. So it is possible to "group" as well the user categories, as the access actions.
So, the command of the first example above could be simplified as follows:
chmod u+rwx,go+r setup.sh
As other Linux commands, chmod can be recursively applied to a folder with all its files and subdirectories. Example: Make a directory
with all its content writable to everyone:
chmod -R ugo+w <directory-name>
Besides the symbolic mode, chmod allows the usage of the octal mode. With this mode, the first parameter of the chmod command is a 3-digits octal number, the digits corresponding (from left to right) to the 3 categories User, Group, and Other. Octal digits may have values from 0 to 7, or binary spoken from 000 to 111. These are 3 binary digits, one for each of the 3 possible actions, from MSB to LSB (from left to right): Read, Write, Execute. If we want the permission for a given action to be set, we set the corresponding bit to 1, otherwise we set it to 0.
Consider the following example:
chmod u+rwx,g+rw,o+r setup.sh
For User, all actions should be allowed, thus the first digit has to be binary 111, corresponding to octal 7. For Group,
reading from and writing to the file should be allowed (the execution of the file denied), thus the second digit has to be binary 110, corresponding to octal 6. For
Other, only reading the should be allowed, thus the third digit has to be binary 100, corresponding to octal 4. And the octal mode command
is:
chmod 764 setup.sh
Other example: If you run a webserver on a Linux machine and upload a Perl script, this script may not be executed by
default. In order to use the script, we have to make it executable by changing the file permissions. Considering the "normal case" for a file (User: read, write; Group
and Other: read), when uploaded the Perl script will have its file permissions in octal mode set to 644. Now, how to do to give everyone the right to run the script? Just
add 1 to each of the 3 digits. So, to make a file executable, use the command:
chmod 755 <file-name>
Interactively changing file permissions.
Maybe, your memory is full of holes, as is mine and you always forget the syntax of the chmod command. Wouldn't it be nice to have some user-friendly interactive program to make the changes? Please, have a look at the Tool to interactively change Linux file permissions in the Lazarus/Free Pascal section of my website. Maybe that it makes things easier for you...
If you find this text helpful, please, support me and this website by signing my guestbook.