Windows Firewall: Allowing intranet computers to access local webserver.
Suppose that you have a Windows computer (in my case a Windows 10 Professional VMware virtual machine named "wk-win10p"), connected to a private network (such as, for example a VMware hostonly network) and that on this machine, you are running an Apache webserver. Suppose that the webserver is configured to listen on standard port 80 on all network interfaces (LISTEN 80 directive in httpd.conf) and that you want to access it not only from localhost, but also from the other computers on the local network (it is supposed that the actual network profile on "wk-win10p" is set to "Private").
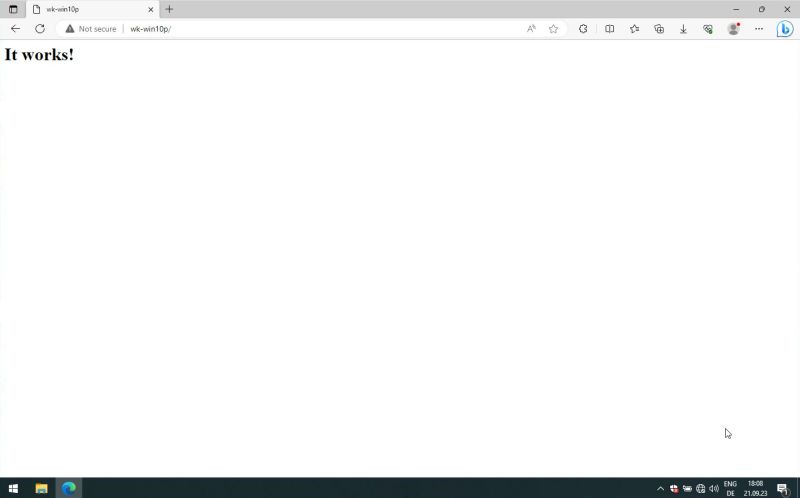
The screenshot below shows the connection to the local website from "wk-win10p" itself using Microsoft Edge as web browser. Successful connection; access to localhost servers is allowed by default on any operating system (I think).
 |
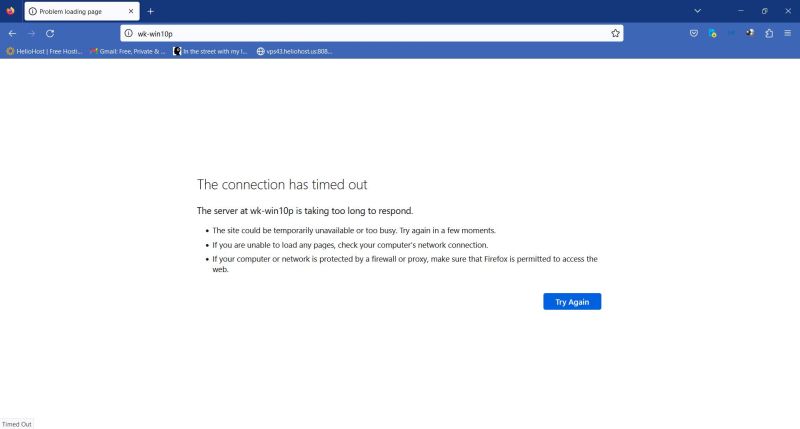
If we try the same from another computer (in my case from "wk-win10", my Windows 10 Home laptop, hosting the VMware virtual machines and connected to "wk-win10p" by a VMware hostonly network, using Firefox as web browser), we'll get a The connection has timed out error message, as shown on the screenshot below.
 |
There could be several reasons for the error message:
- There is a connection problem between the 2 computers. That this is not the case can be easily checked by using the ping command.
- Apache does not listen on the network adapter, to which the other computer is connected to. As we suppose that our Apache listens on all available interfaces, this is not our case.
- The connection is blocked by the firewall on the computer where the webserver is running on.
Connections from other computers are blocked by default by all firewall software, including Windows Defender Firewall, that is running on my "wk-win10p". This tutorial shows how to configure the default Windows 10 firewall to allow access from other intranet computers to a local webserver listening on port 80. I suppose that the tutorial also applies to Windows 8 and Windows 11. If you have installed a third party firewall in replacement of Windows Defender Firewall, have a look at its documentation in order to see how to create inbound firewall rules.
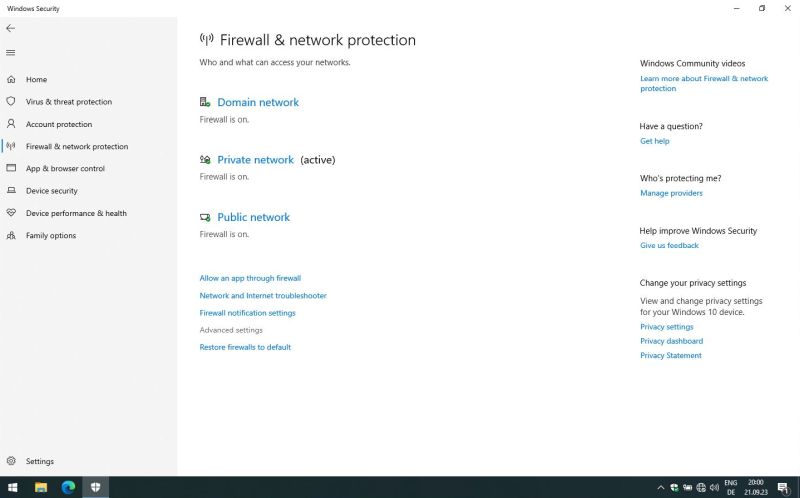
Open Windows Security in the system tray and in the left pane, choose Firewall & network protection. Click the Advanced settings link beneath the Domain, Private and Public network items.
 |
In the Windows Defender Firewall with Advanced Security window, open Inbound Rules (left pane), then choose New rule... (Action pane on the right). The first choice to be made is to select a rule type. For our rule concerning HTTP access to Apache, the most obvious choice is a port based rule.
![Windows Defender Firewall: Creating a new port based inbound rule [1] Windows Defender Firewall: Creating a new port based inbound rule [1]](../screenshots/win_http4.jpg) |
In the next window, we have to indicate the port for which the rule should apply. For our webserver, this is TCP port 80 (screenshot on the left). We have then to choose the rule action; select allow the connection in order to allow other computers to access "wk-win10p" on port 80 (screenshot on the right).
![Windows Defender Firewall: Creating a new port based inbound rule [2] Windows Defender Firewall: Creating a new port based inbound rule [2]](../screenshots/win_http5a.jpg)
|
![Windows Defender Firewall: Creating a new port based inbound rule [3] Windows Defender Firewall: Creating a new port based inbound rule [3]](../screenshots/win_http5b.jpg)
|
Port and action defined, we have to choose a network profile. As we want allow access to Apache from our local intranet, select private network (screenshot on the left). And finally, we have to give a name to the rule (e.g. "Apache HTTP server") and, if we want, we can also add a rule description (screenshot on the right).
![Windows Defender Firewall: Creating a new port based inbound rule [4] Windows Defender Firewall: Creating a new port based inbound rule [4]](../screenshots/win_http6a.jpg)
|
![Windows Defender Firewall: Creating a new port based inbound rule [5] Windows Defender Firewall: Creating a new port based inbound rule [5]](../screenshots/win_http6b.jpg)
|
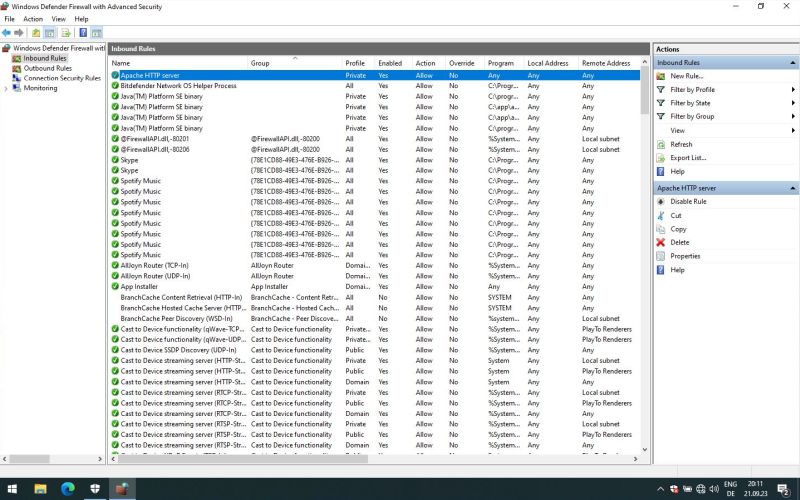
The screenshot below shows the new rule in the Windows Defender Firewall with Advanced Security window. Note that in order to temporarily block HTTP access from other computers, you can simply disable the rule, using the corresponding command in the Action pane.
 |
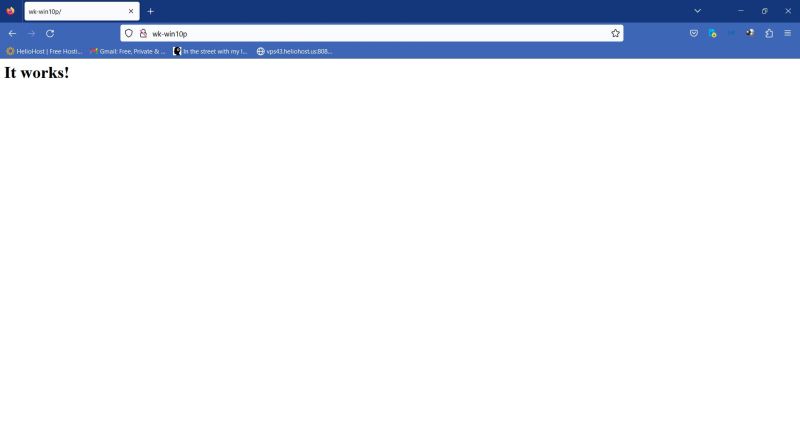
Remains to check if access to Apache is actually possible. On my "wk-win10" machine, I entered http://wk-win10p in the address bar of my Firefox web browser. As you can see on the screenshot, the local website on "wk-win10p" is now accessible from "wk-win10".
 |
If you find this text helpful, please, support me and this website by signing my guestbook.